RSA Token. Two-factor Authentication Device, Hardware. Cryptosystem for Security. Vector Icon Stock Vector - Illustration of protection, object: 147897133

Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey | Kaspersky official blog





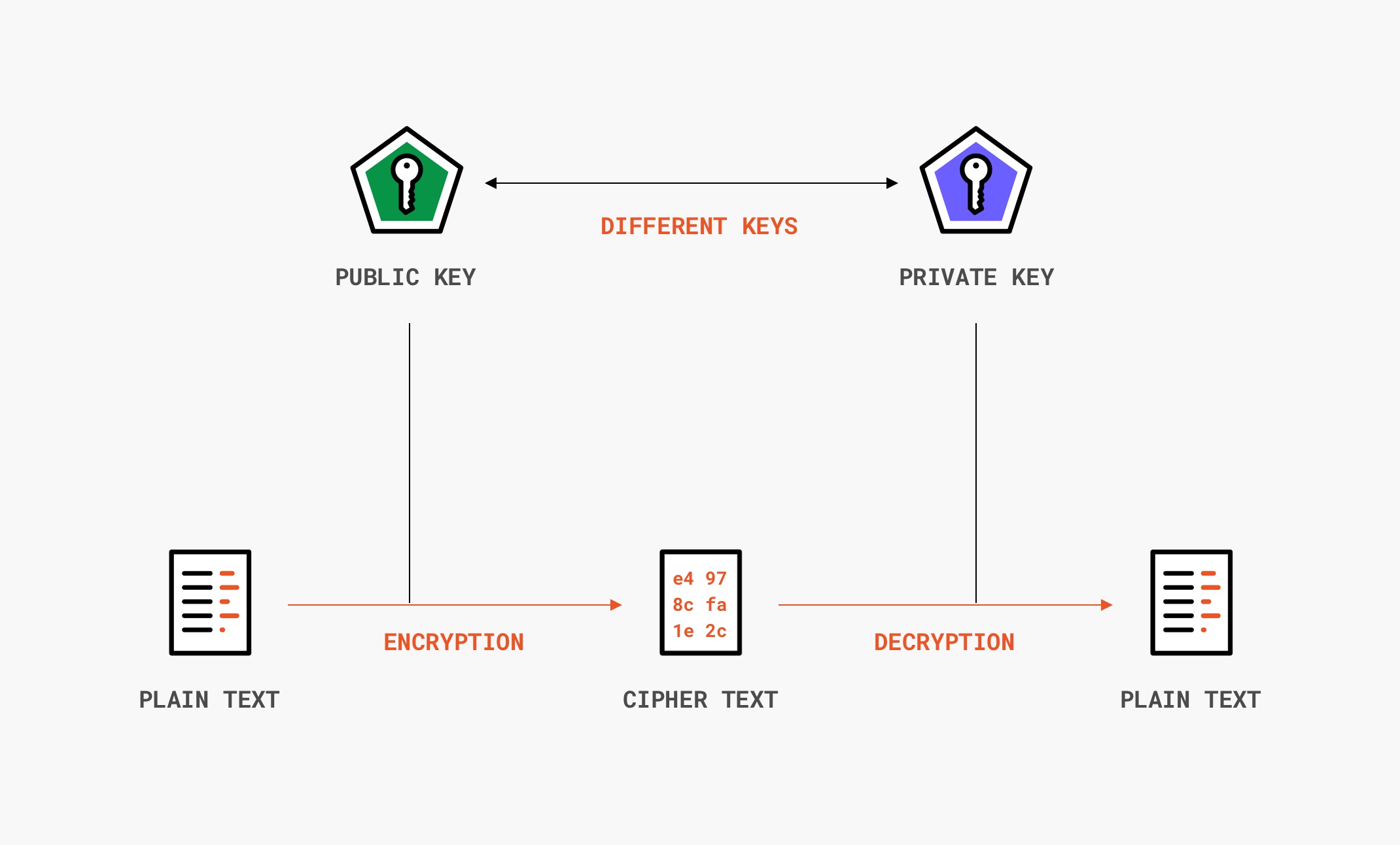
/cdn.vox-cdn.com/uploads/chorus_asset/file/14155906/akrales_190220_3226_0003.jpg)













