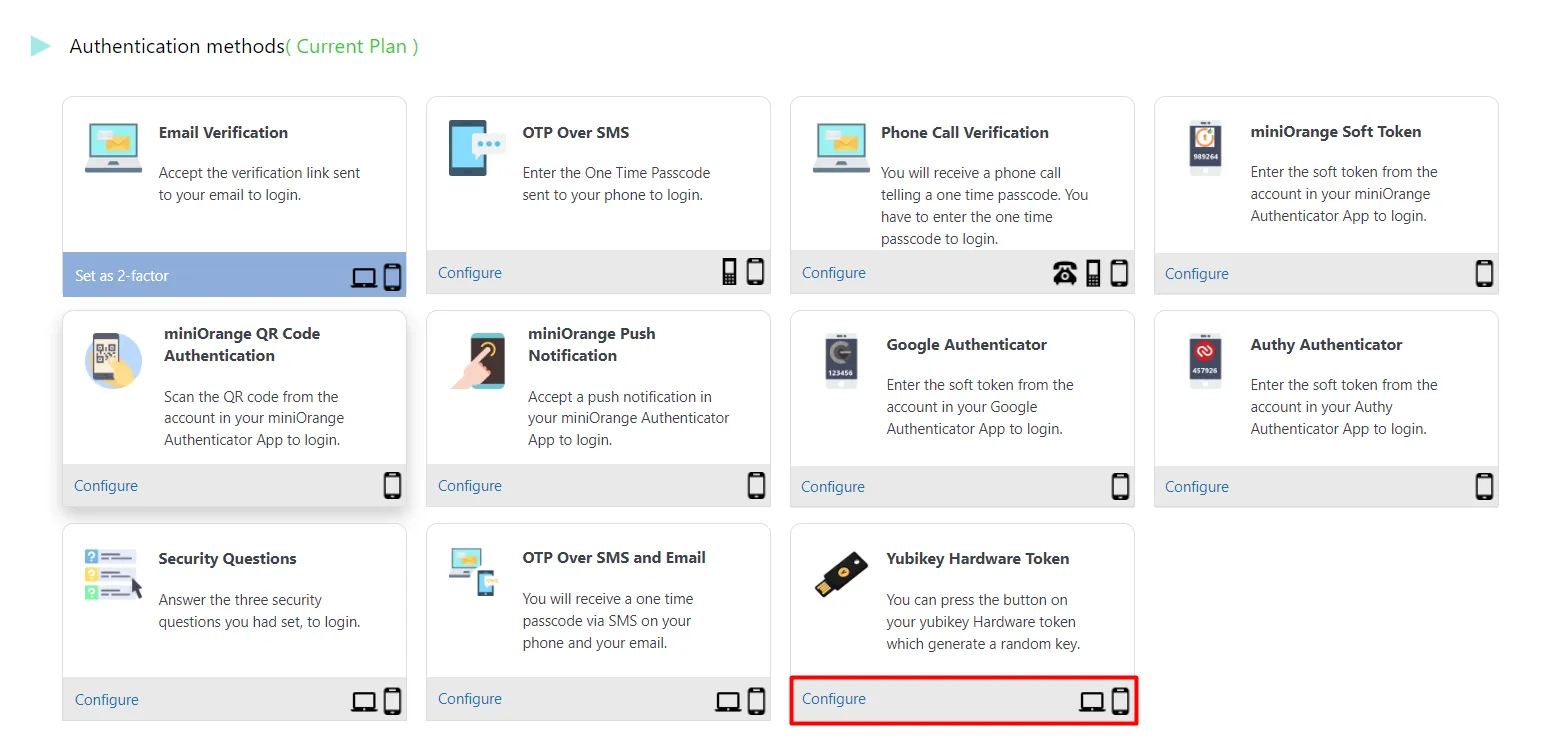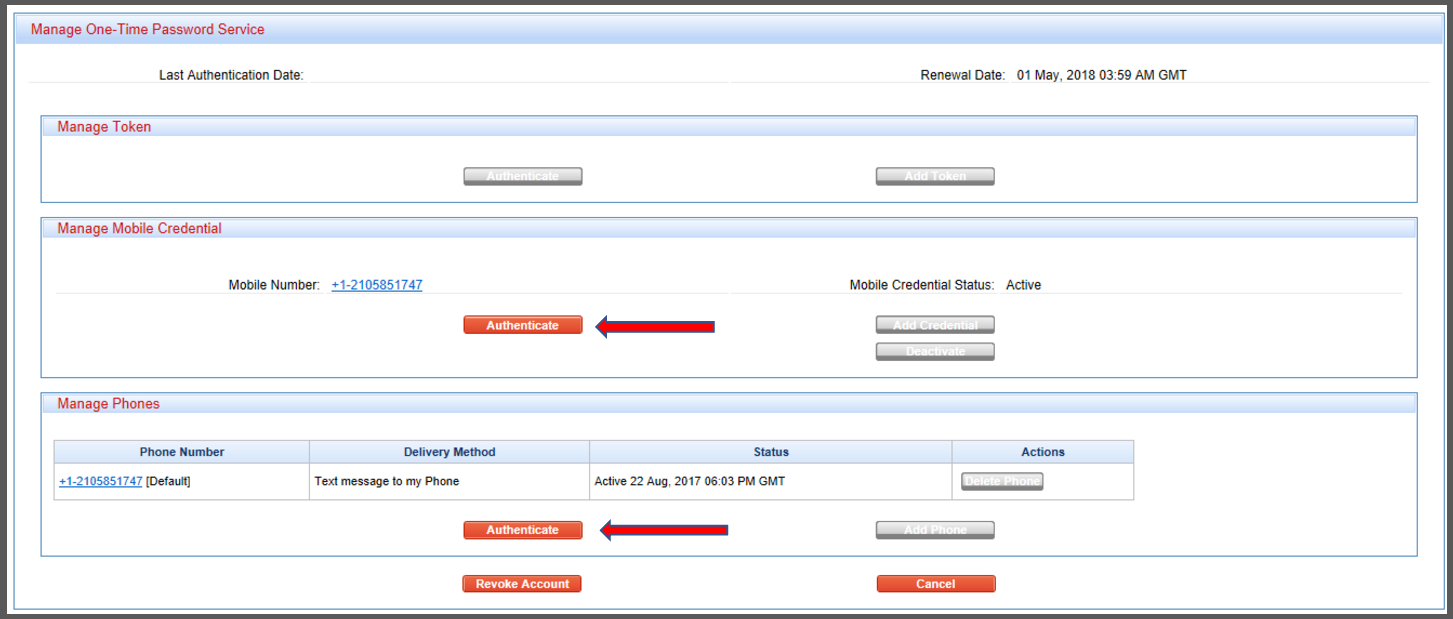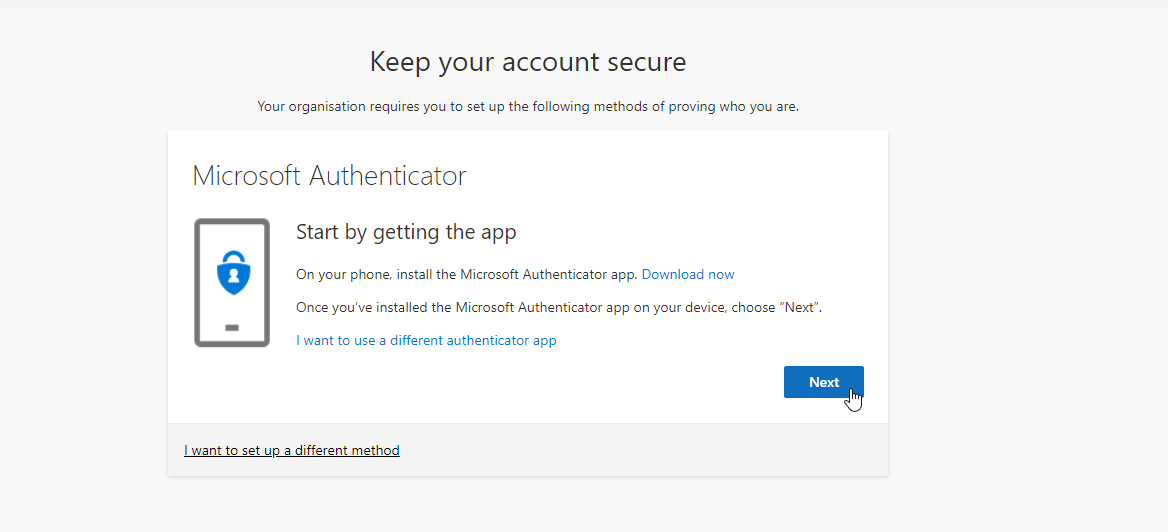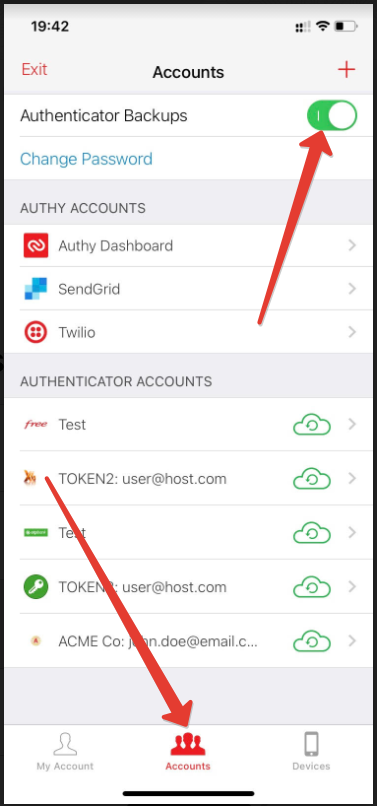
Token2 | Strong authentication with hardware tokens OATH-TOTP SHA-1 SHA-256 | How to transfer TOTP profiles from Authy to a Token2 hardware token | TOKEN2 MFA Products and Services | programmable hardware
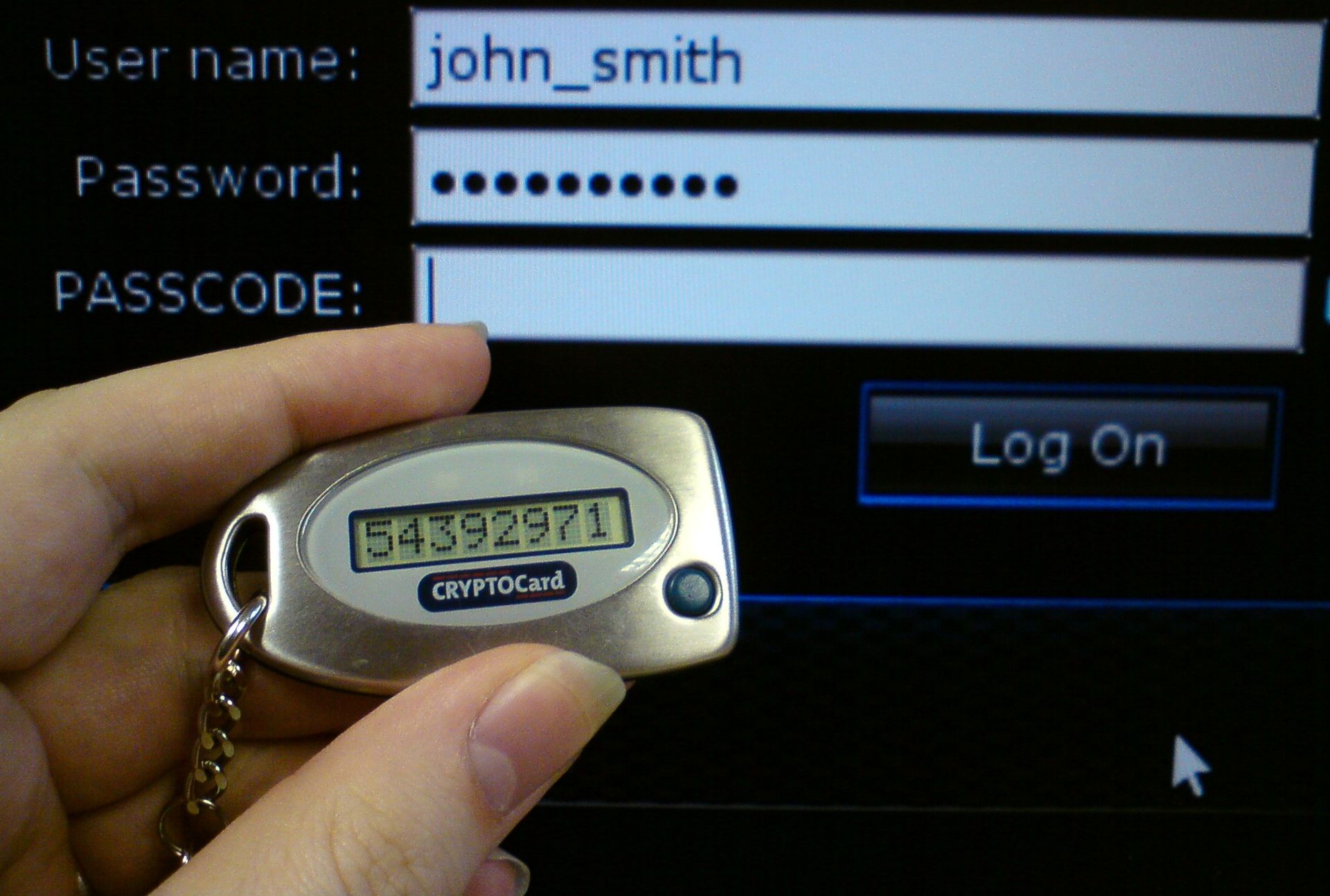
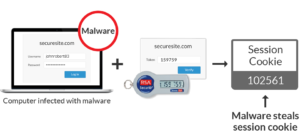
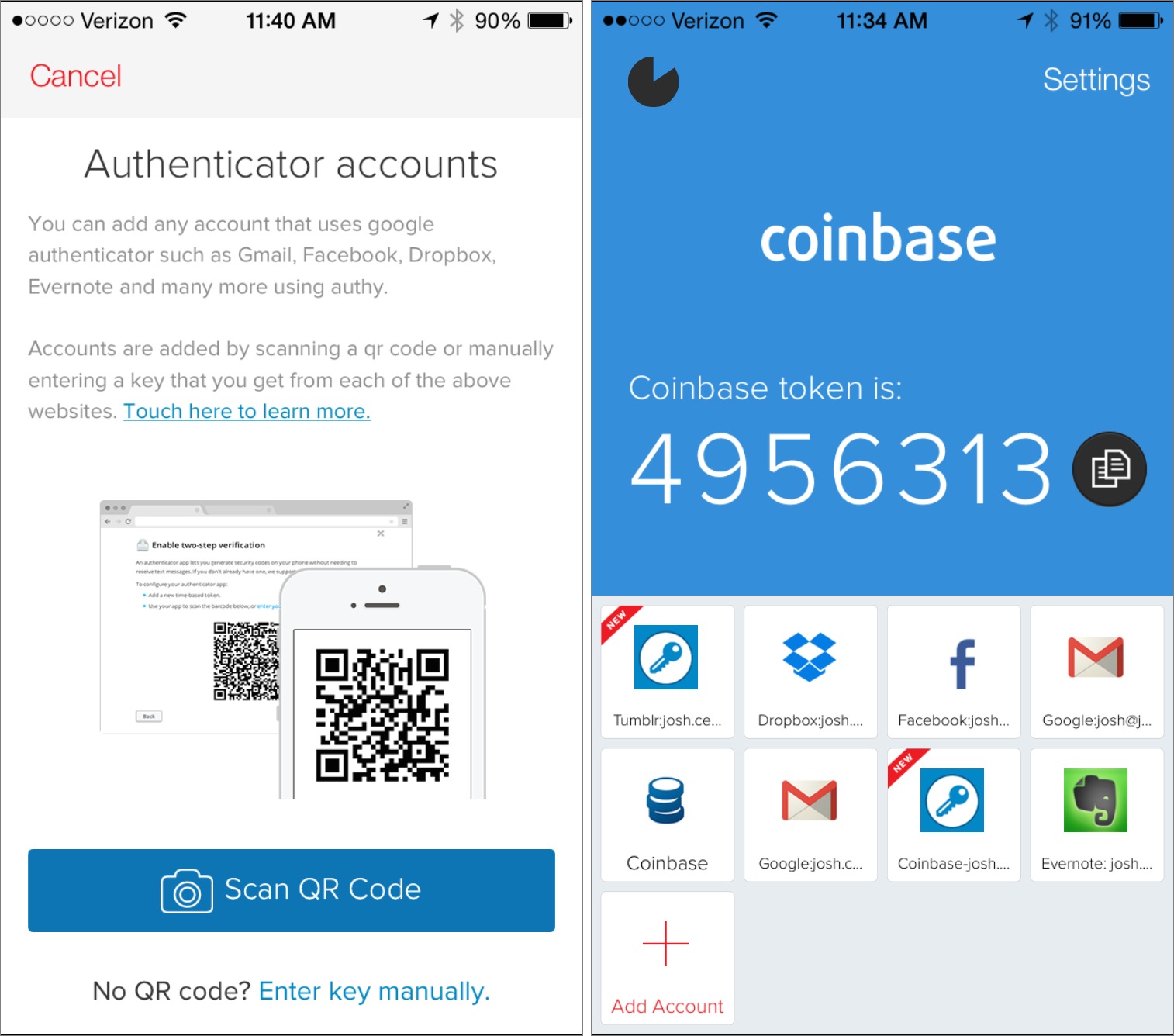
Two Factored Authentication with Twilio Authy – Thihara Neranjya – Fullstack Software Engineer with an affinity for Java.