Google Cloud Designs Hardware Module for Encryption, Sold as a Service | Data Center Knowledge | News and analysis for the data center industry

Encryption Done Right & Drive Configurations - The Crucial/Micron M500 Review (960GB, 480GB, 240GB, 120GB)

Why Hardware Encryption is More Effective Than Software Encryption For Securing The Internet of Things - ELE Times

Kanguru: The One-Stop Solution for AES 256-Bit Hardware Encryption and Fully-Integrated Remote Management | Business Wire
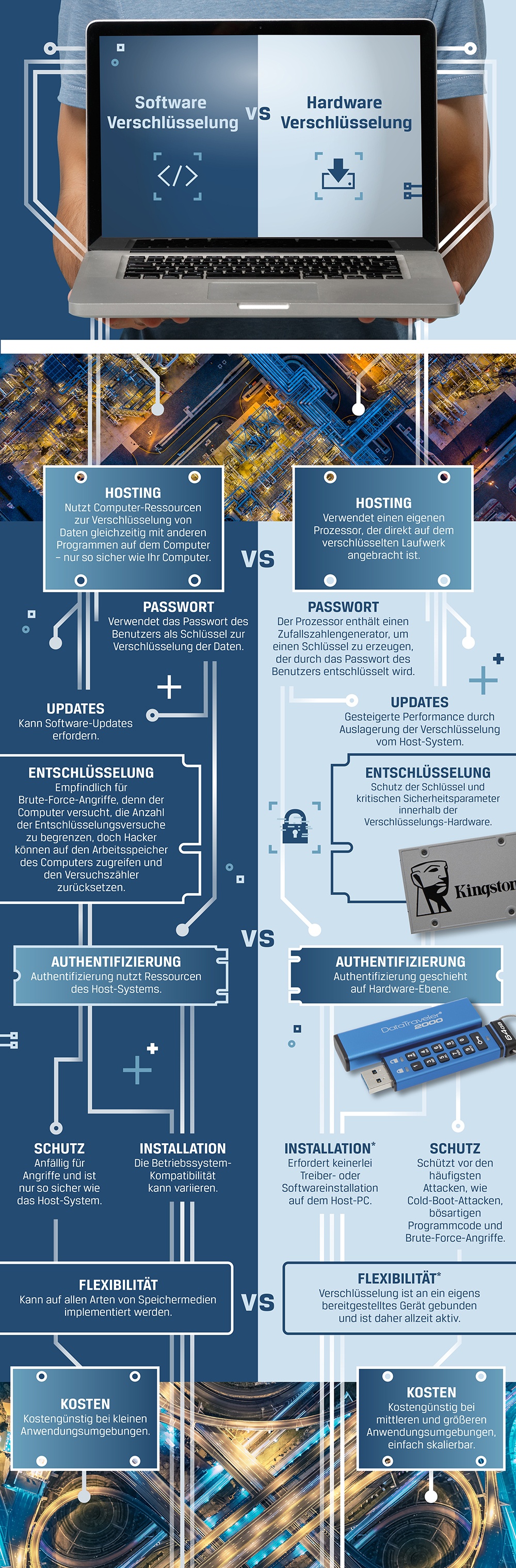
Infografik – Software- vs. Hardware-Verschlüsselung in Client-SSD- und USB-Sticks - Kingston Technology

Kryptor FGPA is a Hardware Security Module that adds Complex Open-source Encryption - Electronics-Lab.com