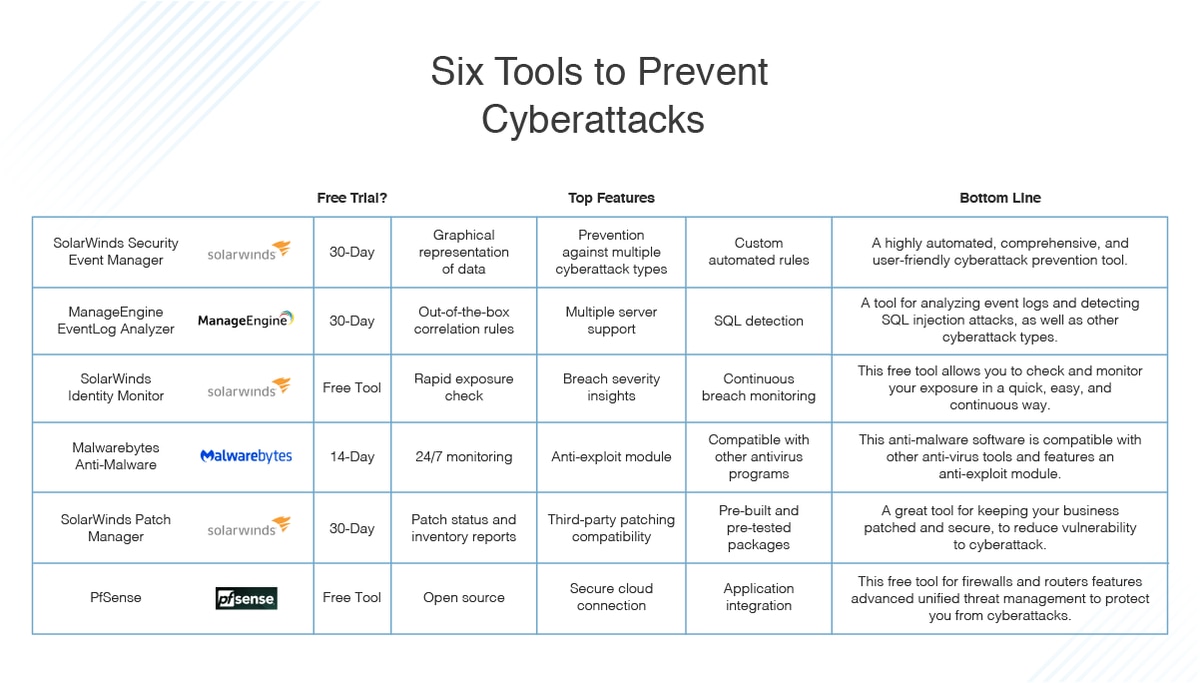
The Hardware Hacking Handbook: Breaking Embedded Security with Hardware Attacks: van Woudenberg, Jasper, O'Flynn, Colin: 9781593278748: Amazon.com: Books

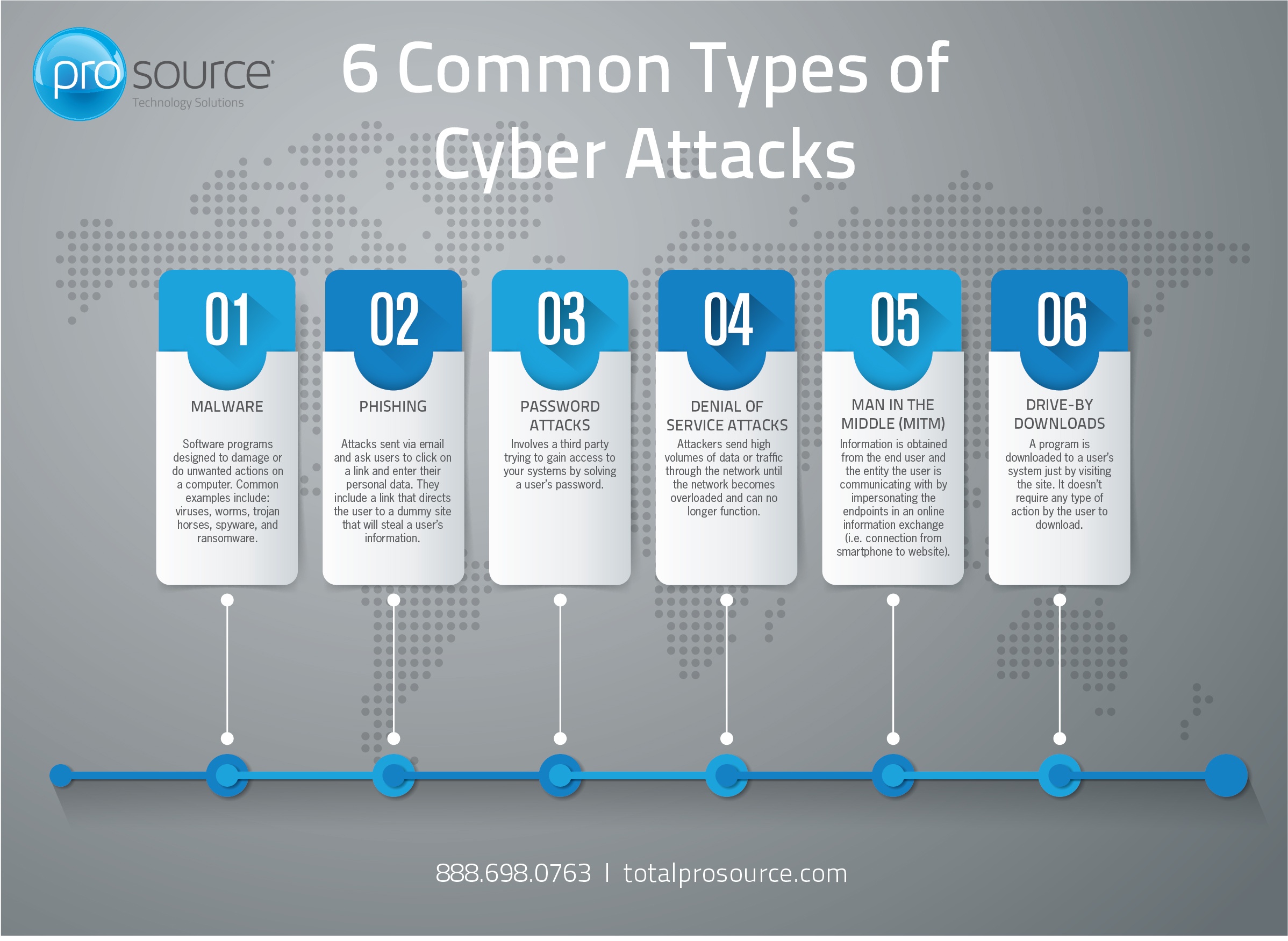
Hardware security knowledge in terms of the hardware-based attacks,... | Download Scientific Diagram