
A Review on Hardware Security Countermeasures for IoT: Emerging Mechanisms and Machine Learning Solutions

Obscure & Undetected: Hacking Into Hardware of Mission-Critical Infrastructure Using Side-Channel Attacks | 2019-11-14 | Security Magazine





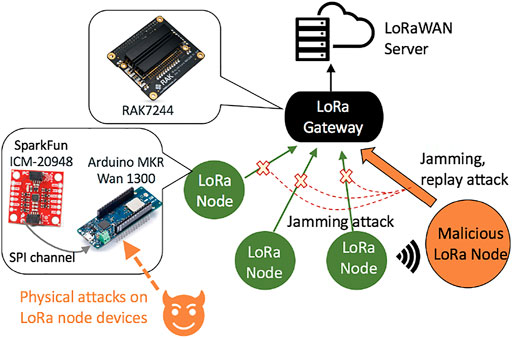

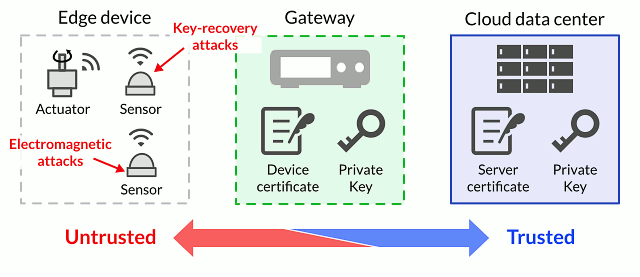








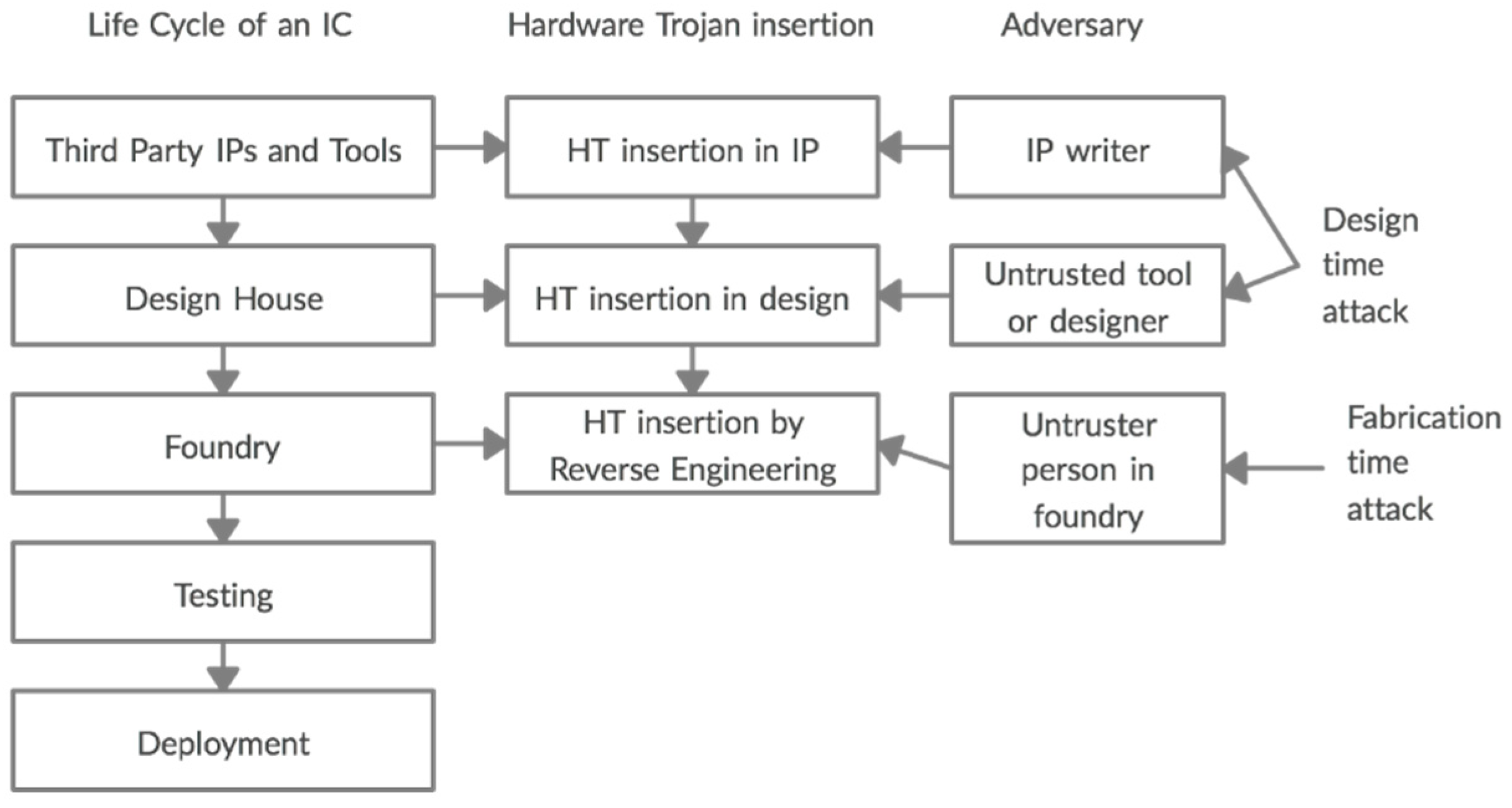



![PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fac9e722cd47fa28222a53bb4d624a42d0d0d04/5-Figure3-1.png)