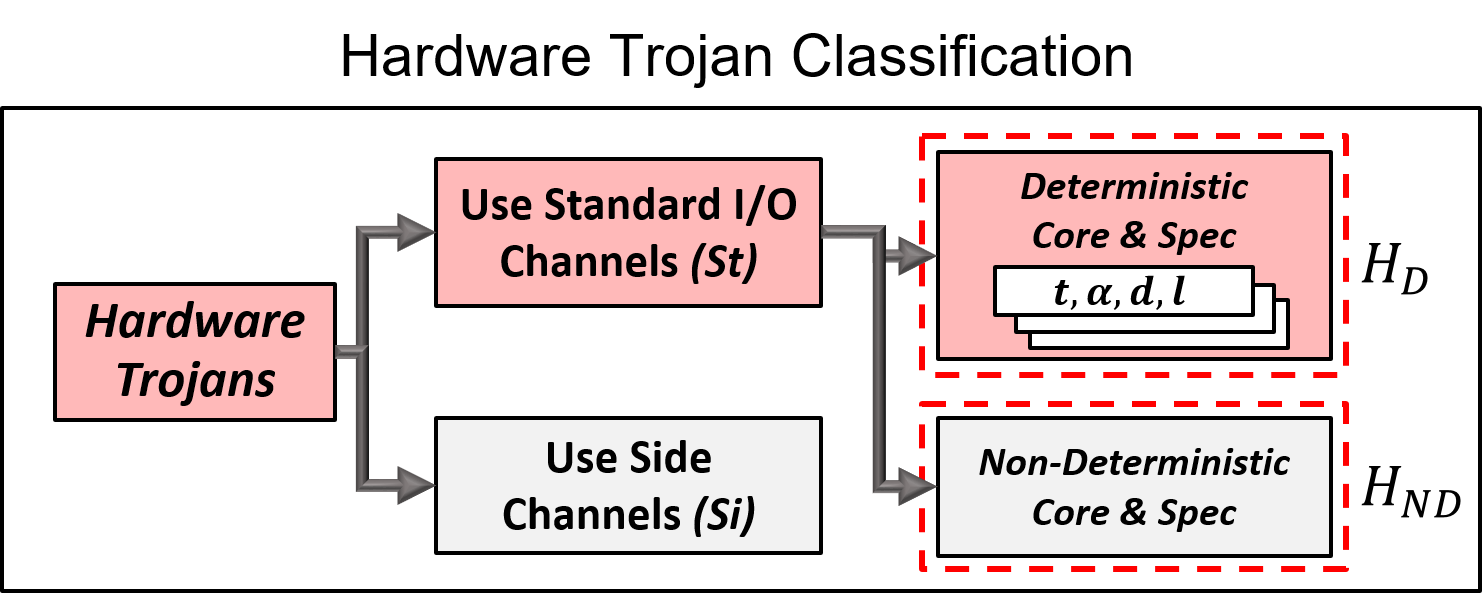
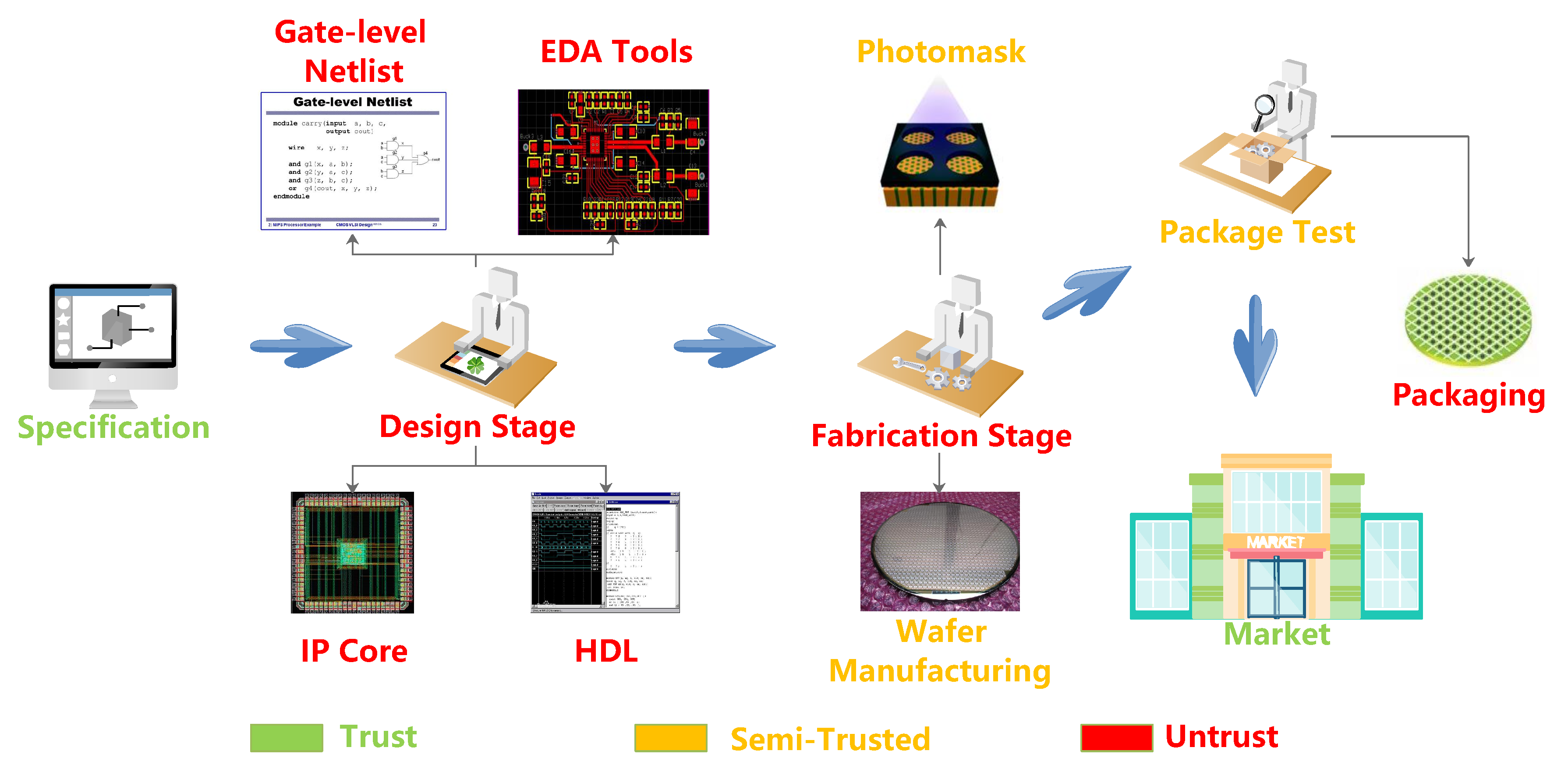
Ten years of hardware Trojans: a survey from the attacker's perspective - Xue - 2020 - IET Computers & Digital Techniques - Wiley Online Library

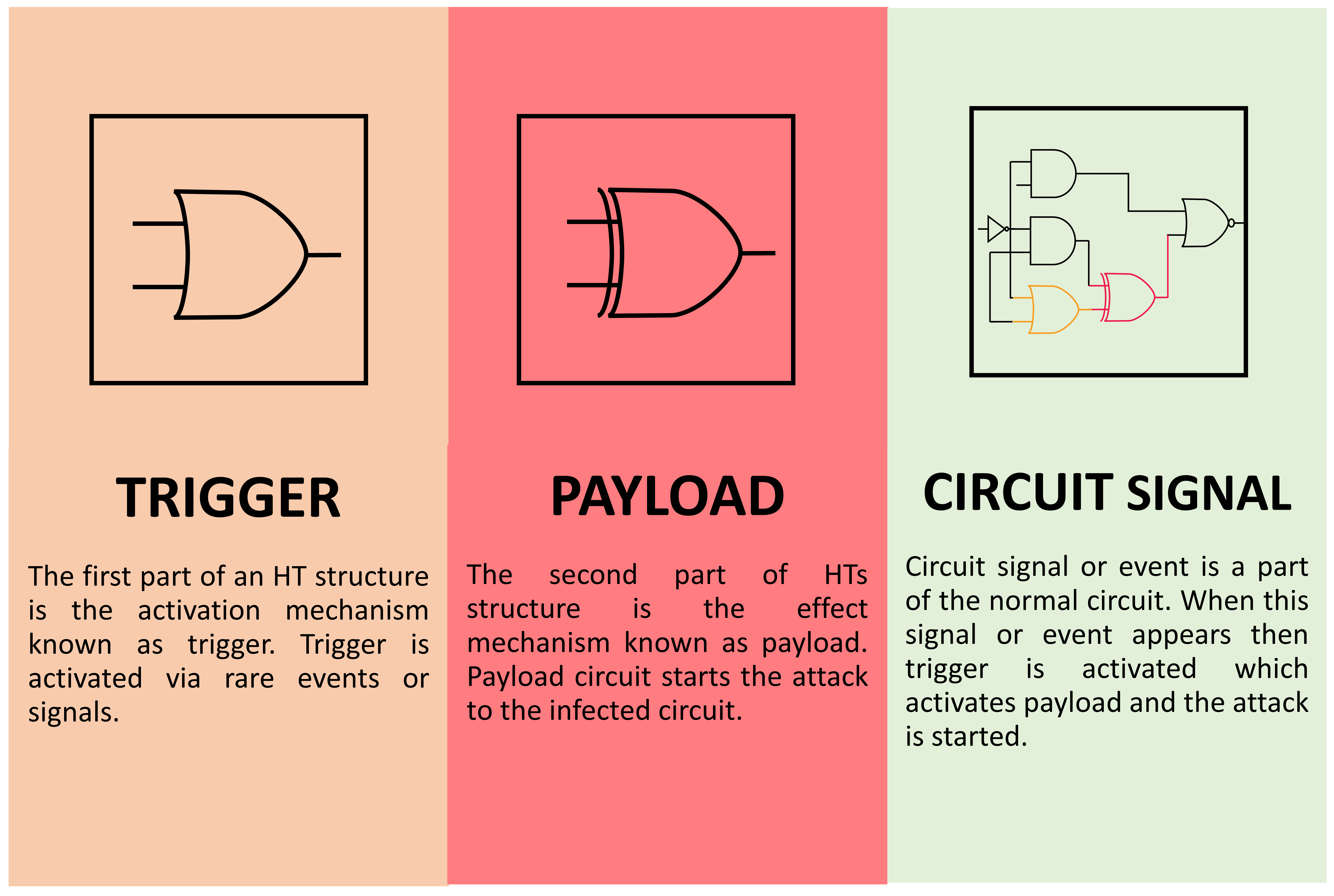
Runtime Identification of Hardware Trojans by Feature Analysis on Gate-Level Unstructured Data and Anomaly Detection

Conventional and machine learning approaches as countermeasures against hardware trojan attacks - ScienceDirect

Understanding – and preventing – the malicious hardware Trojan | EPoCH Project | Results in brief | H2020 | CORDIS | European Commission

Ten years of hardware Trojans: a survey from the attacker's perspective - Xue - 2020 - IET Computers & Digital Techniques - Wiley Online Library
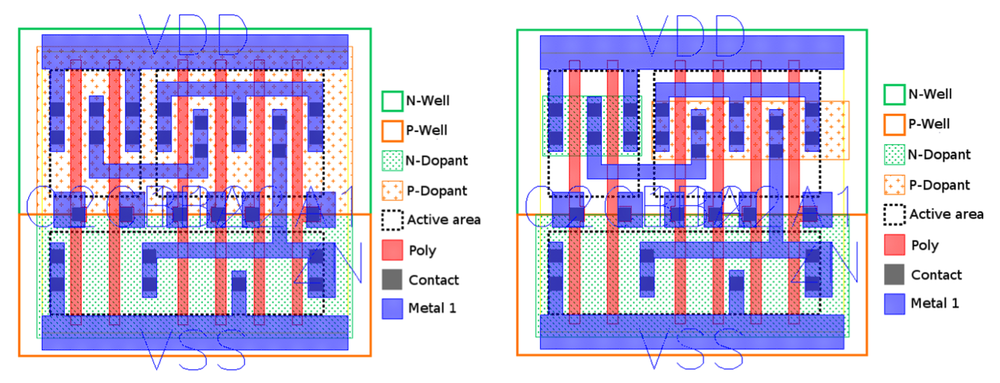
![PDF] Hardware trojan attacks in FPGA devices: threat analysis and effective counter measures | Semantic Scholar PDF] Hardware trojan attacks in FPGA devices: threat analysis and effective counter measures | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e52f44110b632f4f3338045e6d99bc630d2b7ac6/1-Figure1-1.png)
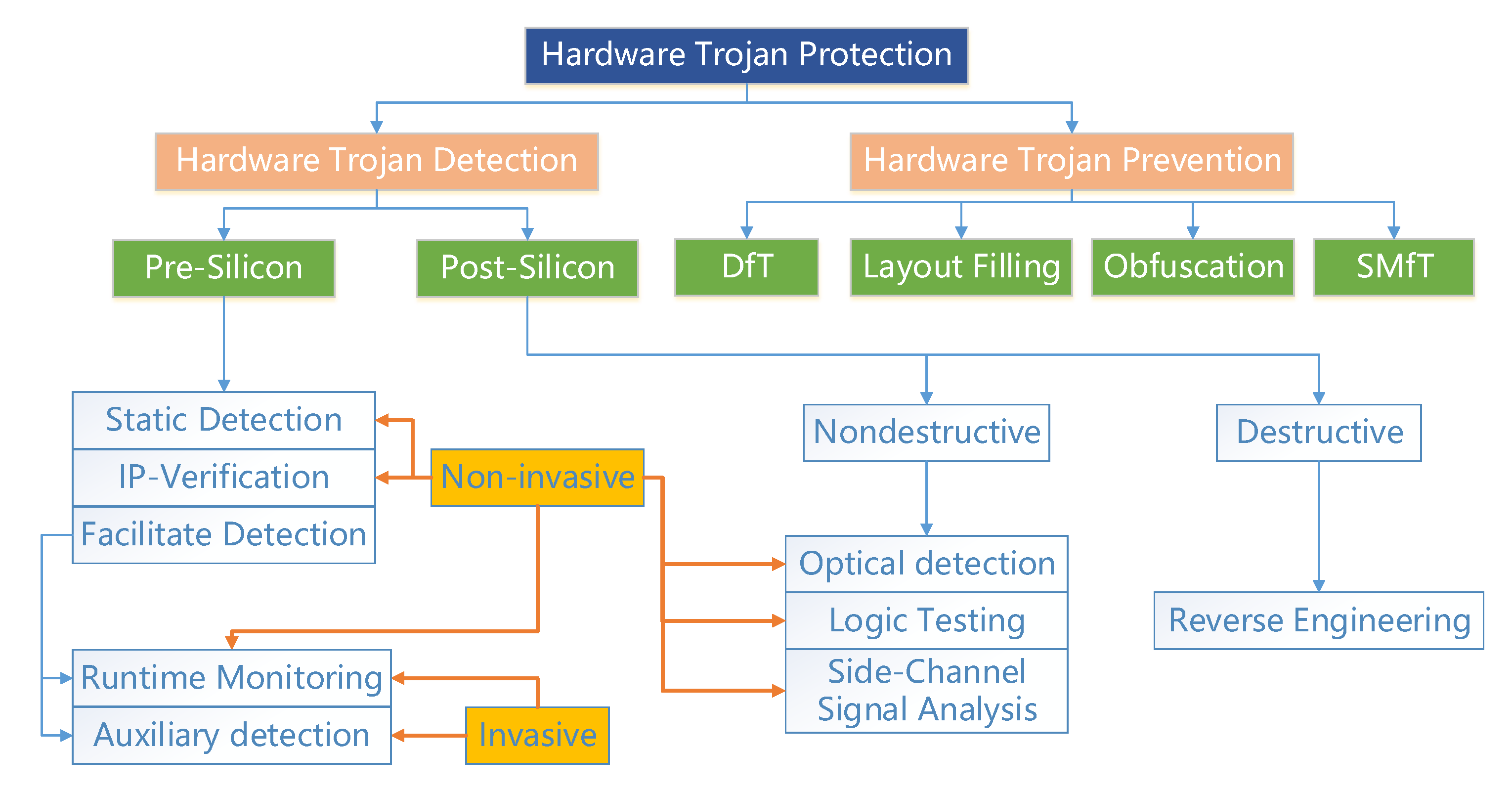

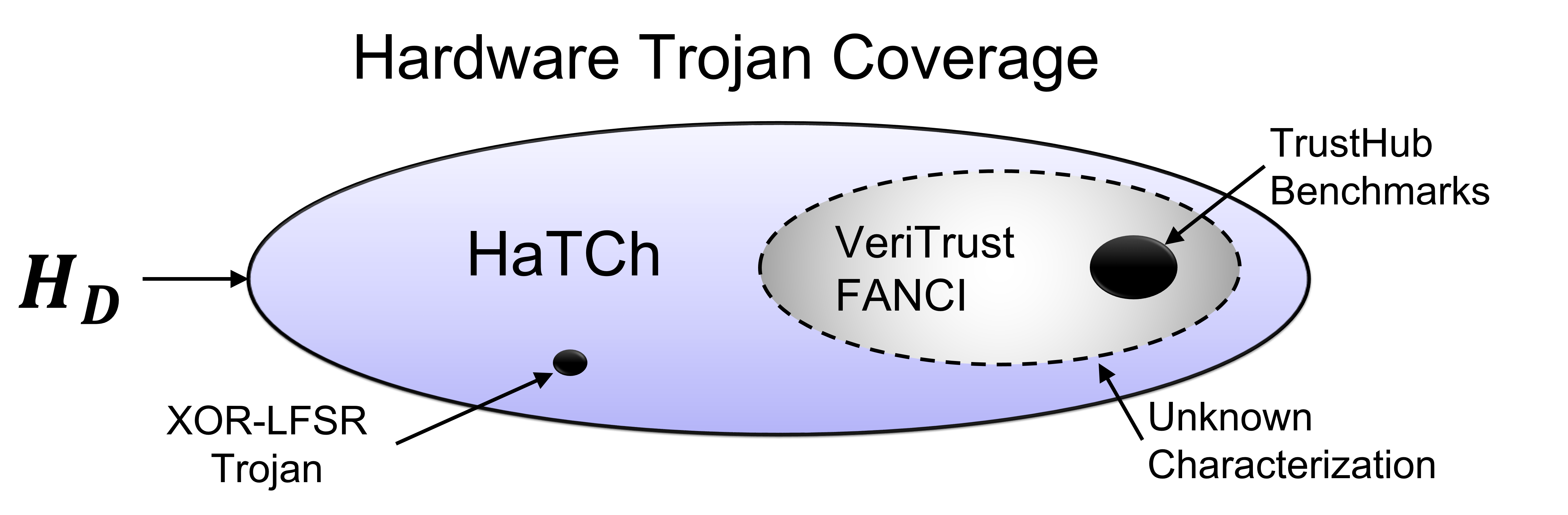

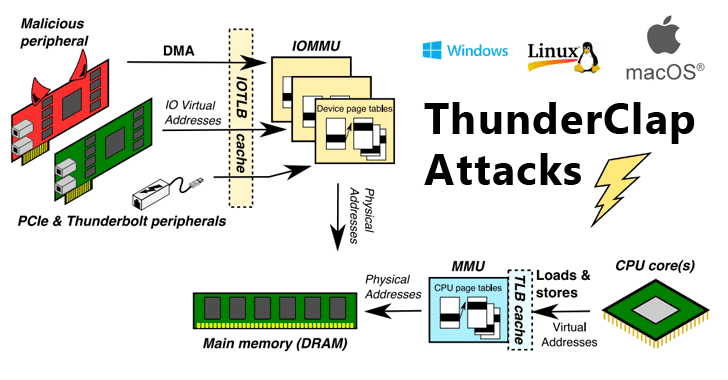




![PDF] Hardware Trojan Attacks on Neural Networks | Semantic Scholar PDF] Hardware Trojan Attacks on Neural Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/621227db6a9b0ad374cf737fea3760b49c4de42c/3-Figure2-1.png)