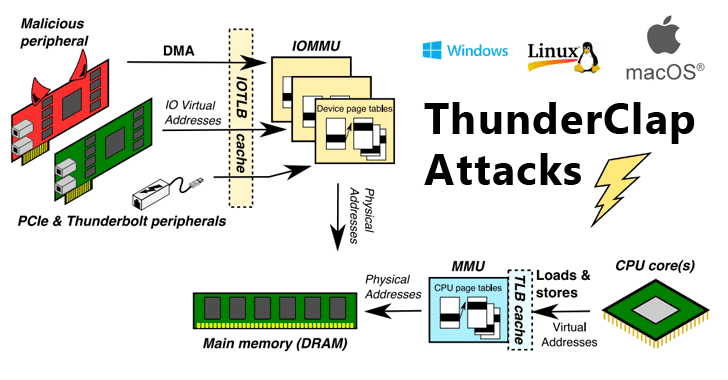
A Stealthy Hardware Trojan Exploiting the Architectural Vulnerability of Deep Learning Architectures: Input Interception Attack

Runtime Identification of Hardware Trojans by Feature Analysis on Gate-Level Unstructured Data and Anomaly Detection

Anomaly Detection with Machine Learning: Charles River Analytics Joins Team AIS to Develop Hardware Trojan Detection Framework - Charles River Analytics
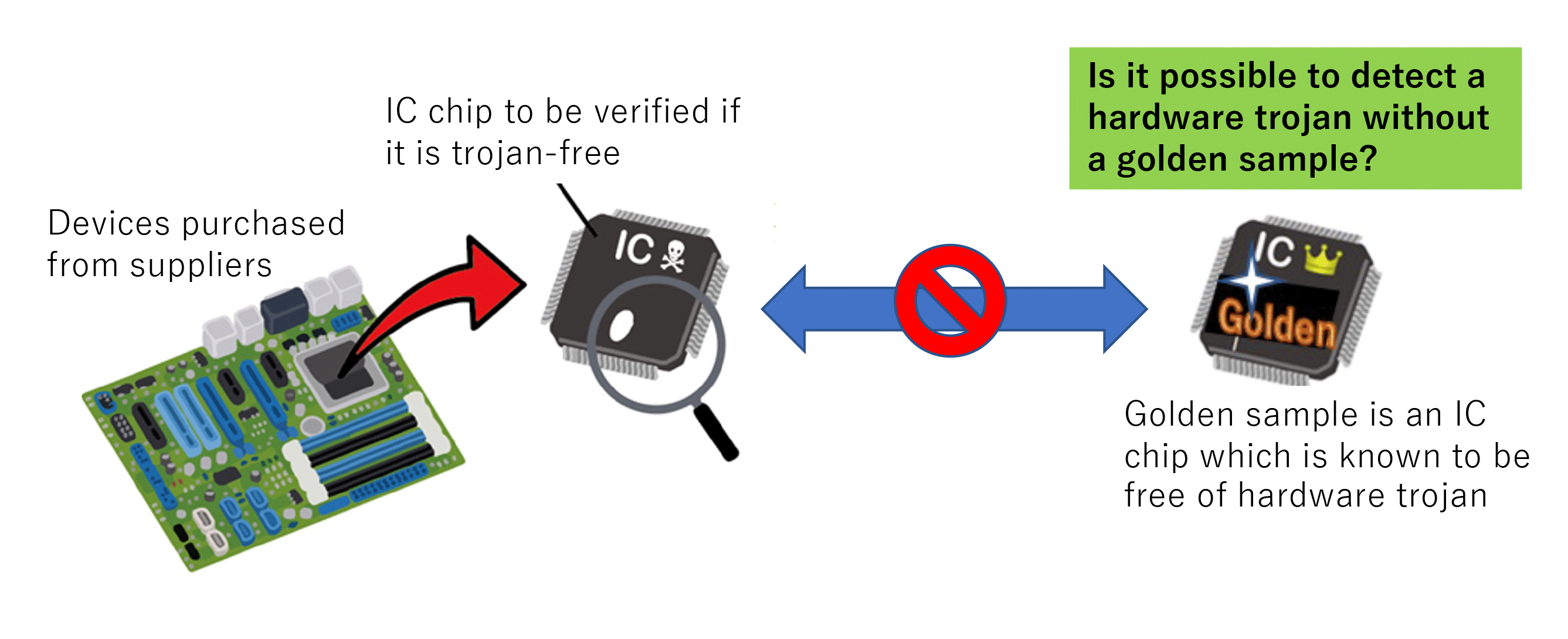
Research on hardware Trojan - Research | Hardware security research team | Cyber physical security reserch cente