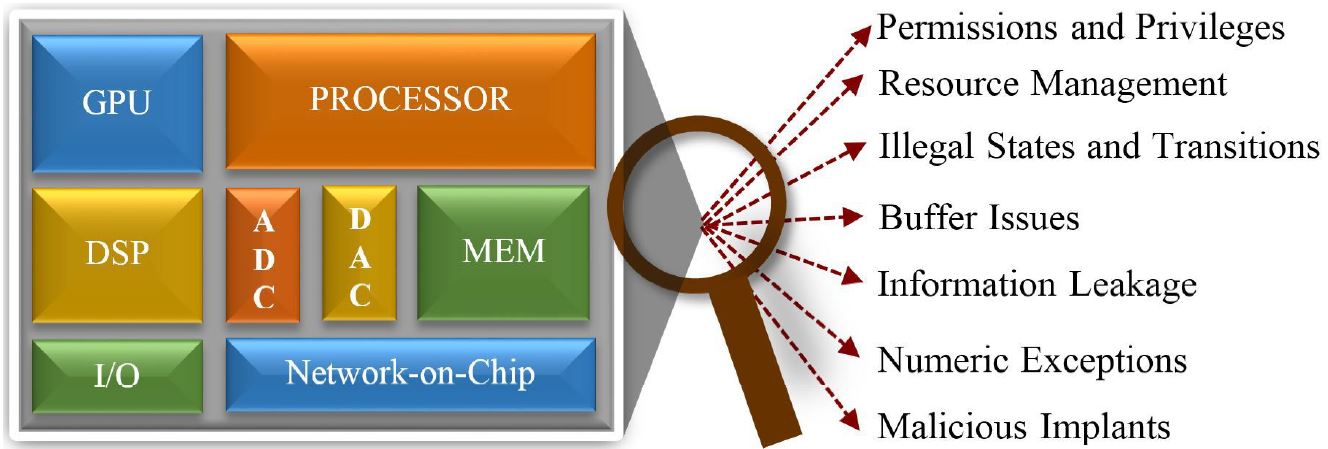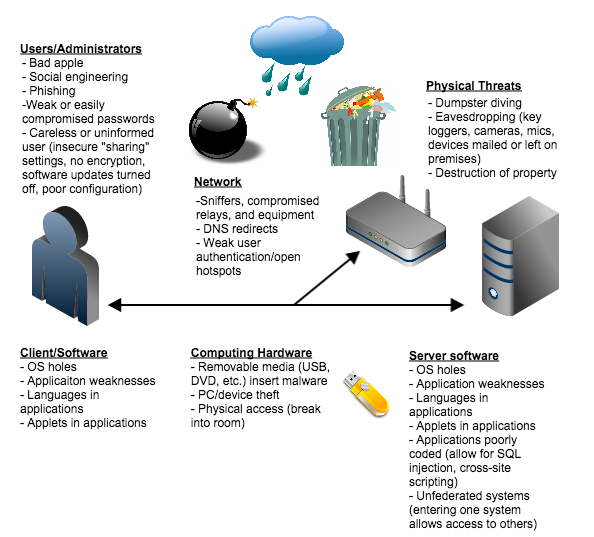
KIT - KIT - Media - Press Releases - Archive Press Releases - Vulnerability of Cloud Service Hardware Uncovered
Defending Against the Unknown: Hardware-Enforced Security and Zero-Day Vulnerabilities | Owl Cyber Defense

Meltdown cpu hardware vulnerability bug isometric composition with computer system board and malicious software symbol vector illustration Stock Vector Image & Art - Alamy