OnlyKey Passwortmanager und FIDO2 / U2F Sicherheitsschlüssel | universelle Zwei-Faktor-Authentifizierung | PGP/SSH/Yubikey OTP | Windows/Linux/Mac OS/Android/iOS: Amazon.de: Computer & Zubehör
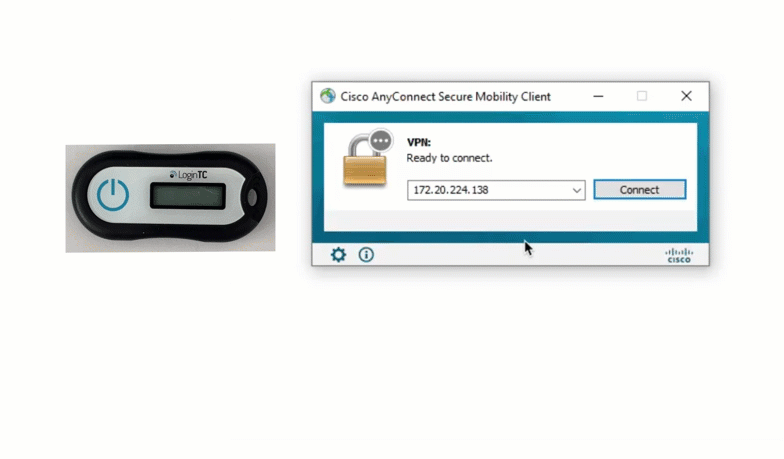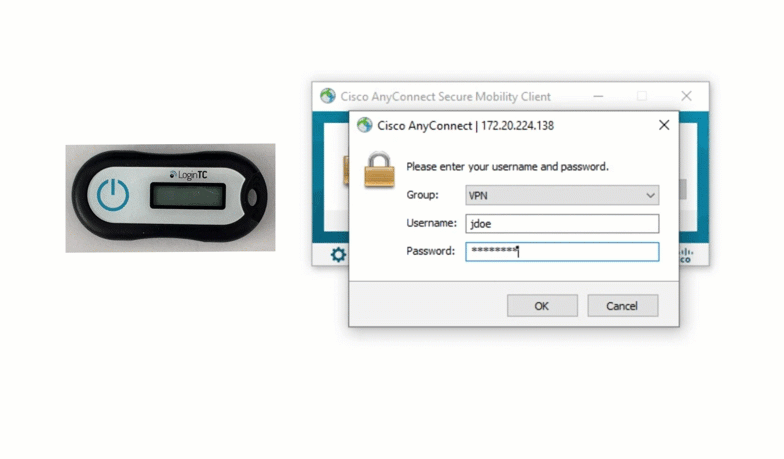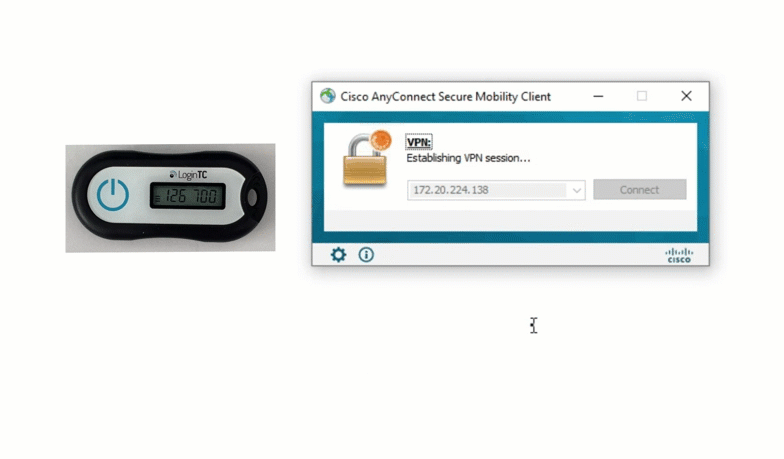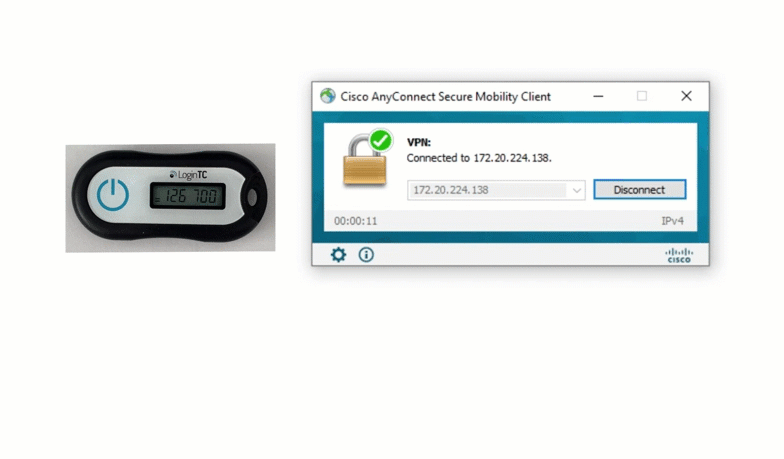
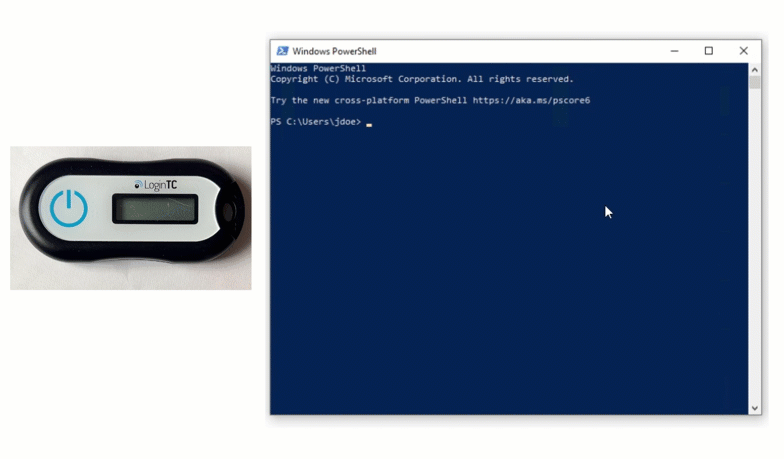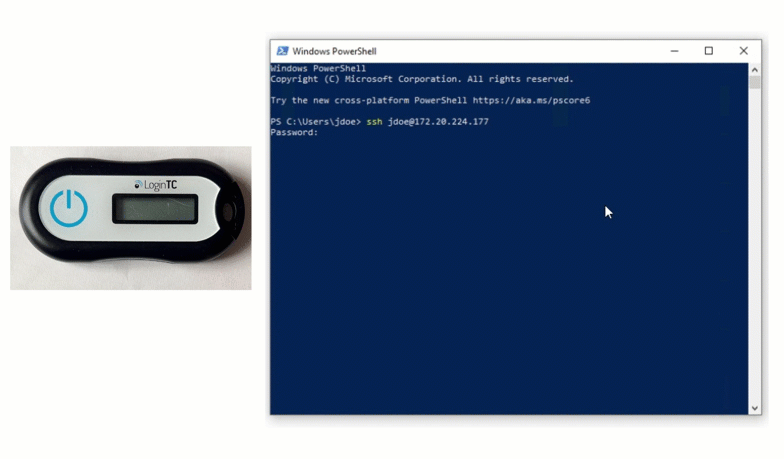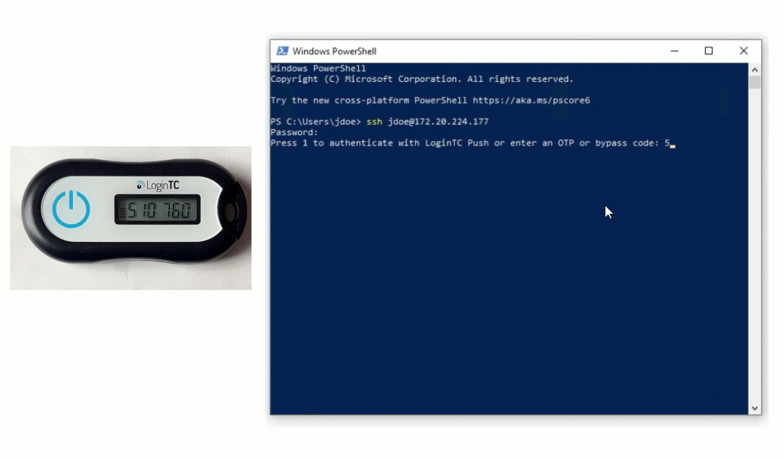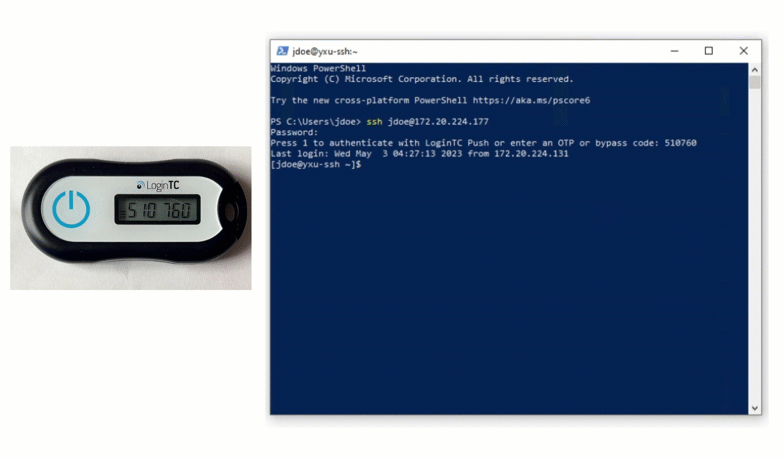
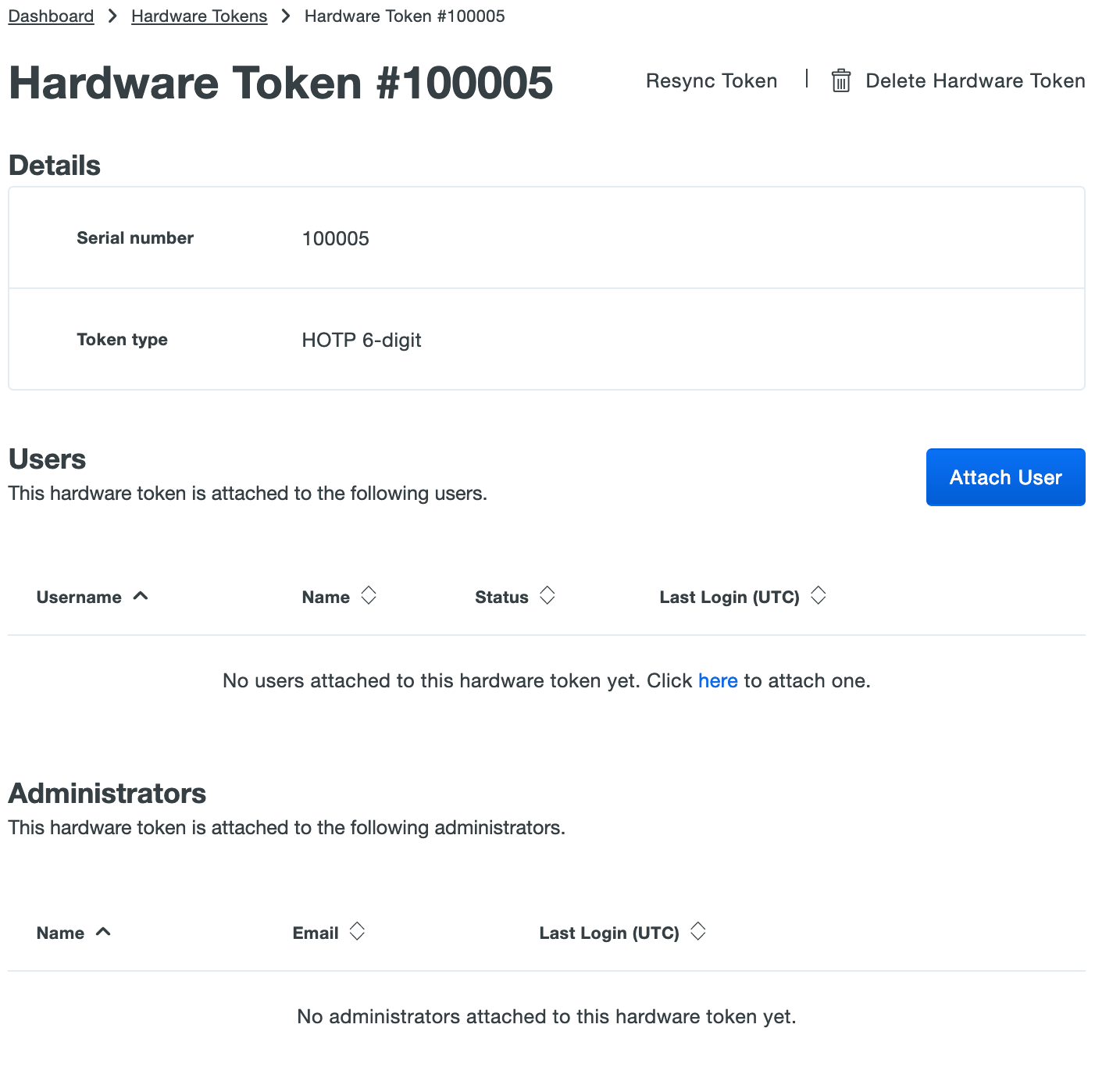
MFA-protected SSH access to Ubuntu servers with LDAP or Azure AD Credentials and hardware or software tokens / Habr